Web applications serve as the backbone of modern business operations. From e-commerce platforms to SaaS solutions, these applications handle sensitive data and critical business processes. However, with great functionality comes great responsibility – and unfortunately, great risk. This is where web penetration testing becomes not just valuable, but essential.
Whether you’re a developer looking to secure your applications, an IT professional expanding your skillset, or a DevOps engineer integrating security into your pipeline, understanding web penetration testing is crucial in today’s threat landscape. This comprehensive guide will walk you through the fundamentals, methodologies, and tools that form the foundation of effective web security assessment.
Understanding the Web Penetration Testing Landscape
Web penetration testing, often called “pen testing” or “ethical hacking,” is the practice of systematically evaluating web applications for security vulnerabilities. Unlike malicious attacks, penetration testing is conducted with explicit permission and aims to identify weaknesses before they can be exploited by actual attackers.
The process mirrors the methodology that real attackers use, but with a crucial difference: the goal is to help organizations strengthen their security posture rather than cause harm. This ethical approach to security testing has become a cornerstone of modern cybersecurity practices.
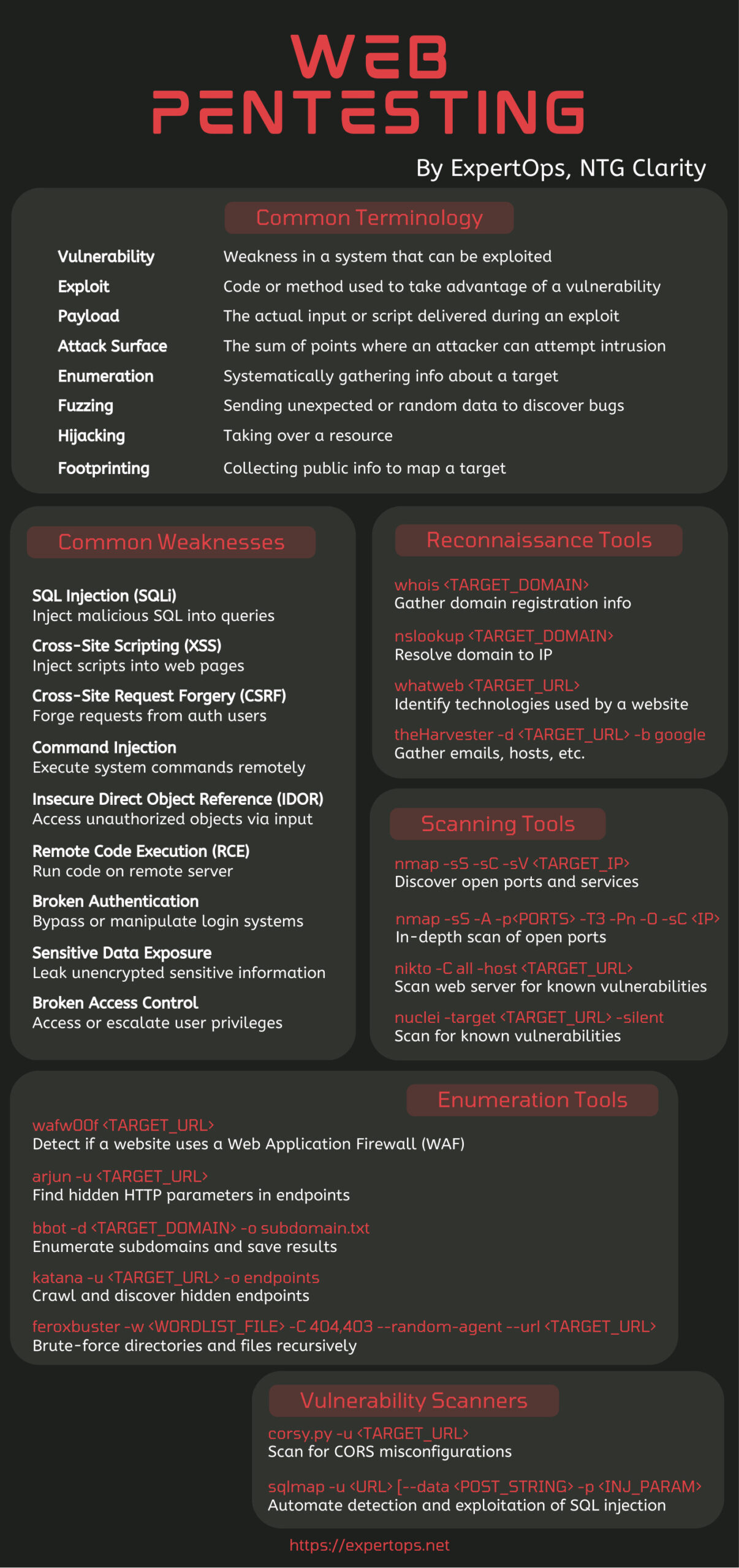
Essential Terminology: Building Your Security Vocabulary
Before diving into the technical aspects, it’s important to understand the key terminology that forms the foundation of web security assessment:
Vulnerability represents any weakness in a system that can potentially be exploited. These aren’t necessarily active threats but rather potential entry points that could be leveraged by attackers.
Exploits are the actual code or methods used to take advantage of identified vulnerabilities. Think of vulnerabilities as unlocked doors and exploits as the specific techniques used to walk through them.
Payloads constitute the actual malicious input or script delivered during an exploit attempt. This is the “ammunition” that gets fired through the vulnerability to achieve the attacker’s objective.
The Attack Surface encompasses all possible points where an attacker might attempt intrusion. In web applications, this includes every input field, parameter, endpoint, and interaction point that accepts user data.
Enumeration involves systematically gathering information about a target system. This reconnaissance phase is crucial for understanding the application’s structure, technologies, and potential weak points.
Fuzzing refers to the practice of sending unexpected, random, or malformed data to application inputs to discover bugs and vulnerabilities. It’s like stress-testing every input to see what breaks.
Hijacking in the context of web security typically refers to taking over user sessions, resources, or even entire applications through various attack vectors.
Footprinting is the process of collecting publicly available information to map and understand a target system. This passive reconnaissance forms the foundation of any thorough security assessment.
The Most Critical Web Application Vulnerabilities
Understanding common vulnerabilities is essential for both offensive and defensive security practices. Here are the most prevalent weaknesses that penetration testers encounter:
SQL Injection (SQLi)
SQL Injection remains one of the most dangerous and common vulnerabilities. It occurs when malicious SQL code is injected into application queries, potentially allowing attackers to access, modify, or delete database information. The impact can range from data theft to complete system compromise.
Cross-Site Scripting (XSS)
XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. These attacks can steal session cookies, redirect users to malicious sites, or perform actions on behalf of the victim.
Cross-Site Request Forgery (CSRF)
CSRF attacks trick users into performing unintended actions on applications where they’re authenticated. This vulnerability exploits the trust that applications have in authenticated users.
Command Injection
This vulnerability allows attackers to execute system commands remotely on the server hosting the web application. The potential impact includes complete system compromise and data exfiltration.
Insecure Direct Object Reference (IDOR)
IDOR vulnerabilities occur when applications provide direct access to objects based on user input without proper authorization checks. This can lead to unauthorized access to sensitive data or functionality.
Remote Code Execution (RCE)
RCE vulnerabilities allow attackers to run arbitrary code on remote servers. This represents one of the most severe types of vulnerabilities, often leading to complete system compromise.
Authentication and Access Control Issues
Broken authentication mechanisms and inadequate access controls can allow attackers to bypass login systems or escalate their privileges within applications.
Sensitive Data Exposure
Many applications fail to properly protect sensitive information, leading to data leaks that can have severe business and legal consequences.
Reconnaissance: The Foundation of Effective Penetration Testing
Successful penetration testing begins long before any actual testing takes place. The reconnaissance phase involves gathering comprehensive information about the target application and its infrastructure.
Domain Intelligence Gathering
Tools like whois provide valuable domain registration information, while nslookup helps resolve domains to IP addresses. The whatweb tool can identify technologies used by web applications, providing insights into potential attack vectors.
Services like theHarvester can gather emails, hosts, and other valuable information from public sources, helping build a comprehensive picture of the target organization’s digital footprint.
Port and Service Discovery
Network scanning tools like nmap form the backbone of infrastructure reconnaissance. Basic port scans using nmap -sS -sC -sV <TARGET_IP> can discover open ports and services, while more comprehensive scans using nmap -sS -A -p<PORTS> -T3 -Pn -O -sC <IP> provide detailed service and operating system information.
Web Application Enumeration
Specialized tools like nikto can scan web servers for known vulnerabilities and misconfigurations. The gobuster tool excels at finding hidden HTTP parameters in endpoints, while ffuf can be used to discover hidden directories and files.
For subdomain enumeration, tools like katana can crawl and discover hidden endpoints, while sublist3r and similar tools can identify subdomains that might host additional attack surfaces.
Directory and file brute-forcing using tools like feroxbuster can reveal hidden administrative interfaces, backup files, and other sensitive resources that weren’t intended for public access.
Vulnerability Assessment and Scanning
While manual testing provides the deepest insights, automated scanning tools play a crucial role in comprehensive security assessments. These tools can quickly identify common vulnerabilities and provide a baseline for further manual investigation.
Web Application Firewalls (WAFs) detection using tools like wafw00f helps testers understand the defensive measures in place and adapt their testing methodology accordingly.
Vulnerability scanners can identify CORS misconfigurations, which can lead to cross-origin attacks, and SQL injection vulnerabilities through automated parameter testing.
However, it’s important to remember that automated tools are just the starting point. The most critical vulnerabilities often require manual testing and creative thinking to discover and properly assess their impact.
Building Your Practical Skills
Web penetration testing is fundamentally a hands-on discipline. While understanding theory is important, developing practical skills requires regular practice in controlled environments.
Consider setting up local testing environments using vulnerable applications like DVWA (Damn Vulnerable Web Application), WebGoat, or Mutillidae. These platforms provide safe, legal environments to practice your skills without risking legal issues or causing unintended damage.
Focus on understanding not just how to use tools, but why certain vulnerabilities exist and how they can be prevented. This holistic understanding will make you more effective whether you’re testing applications or building secure ones.
The Professional Landscape
As organizations increasingly recognize the importance of proactive security measures, the demand for skilled penetration testers continues to grow. However, entering this field requires more than just technical skills – it demands a strong ethical foundation, excellent communication abilities, and a commitment to continuous learning.
Professional penetration testers must be able to clearly communicate complex technical issues to both technical and non-technical stakeholders. The ability to provide actionable recommendations and help organizations improve their security posture is just as important as finding vulnerabilities.
Partnering with ExpertOps for Comprehensive Security
While developing internal security capabilities is valuable, many organizations benefit from partnering with experienced penetration testing firms. At ExpertOps, we bring years of specialized expertise to help organizations identify and address security vulnerabilities before they can be exploited by malicious actors.
Our security consultation service covers the full spectrum of web application security assessment, from initial reconnaissance through detailed vulnerability analysis and remediation guidance. We work closely with development teams, IT departments, and leadership to ensure that security improvements are practical, effective, and aligned with business objectives.
Whether you’re looking to validate the security of a new application, comply with regulatory requirements, or simply gain confidence in your security posture, our team provides the expertise and objectivity that comes from extensive experience across diverse industries and technologies.
Moving Forward: Your Next Steps
Web penetration testing represents a critical skill set in today’s security landscape. Whether you’re building applications, managing infrastructure, or working to secure organizational assets, understanding these concepts and methodologies will enhance your effectiveness and career prospects.
Start by familiarizing yourself with the tools and techniques outlined in this guide. Practice in legal, controlled environments, and consider pursuing formal training or certifications to validate your skills. Most importantly, remember that security is an ongoing process, not a one-time event.
The attached cheatsheet provides a quick reference for the tools and techniques discussed in this article. Keep it handy as you develop your skills and begin applying these concepts in your own security assessments.
Remember: with the power to identify and exploit vulnerabilities comes the responsibility to use these skills ethically and constructively. The goal is always to improve security, protect users, and help organizations better defend against real threats.
Ready to take your organization’s security to the next level? Contact ExpertOps today to learn how our security consultation service can help identify vulnerabilities and strengthen your security posture.
